Showing posts with label Security. Show all posts
Simple DOs and DON’Ts For Your Security
Junaid
On
 While you start playing with internet, the next important thing is your security. One should take serious steps for his/her security while using internet as people are scamming everywhere. Following are some DOs and DON'Ts tips to be secured.
While you start playing with internet, the next important thing is your security. One should take serious steps for his/her security while using internet as people are scamming everywhere. Following are some DOs and DON'Ts tips to be secured.1. Never click on links in emails, unless you are either expecting them
or know for sure they are what they appear to be. When you see a link in
your email hover your mouse pointer over it and make sure the address
matches up to what you see in your email. Many phishing emails appear to be from A but when clicked on they take you to B, so B-ware.
2. Look out for dodgy PayPal links in your email. I don’t even trust genuine PayPal emails anymore. Phishing scams have become so sophisticated that people will send you emails that look identical to genuine PayPal emails and can trick the untrained eye into sending cash to scammers. One way to decipher the real from the fake is by looking at the address of the email. When you get one from PayPal it will be from the paypal.com domain and not offshoreaccountants.ng.
3. Don’t use file sharing programs to download software. Apps like Kazaa, limewire etc host a myriad of infected and dangerous software just waiting to enter your PC. PC software is not too expensive, and a lot of the more useful programs are often free and open-source. So there’s really no need to be using these programs. You just don’t know what you’re getting. Not to mention that you should be paying for the software you use.
4. Beware of links in Instant Messenger clients like Yahoo Messenger, Steam, Windows Live, Skype etc. Just like the email you can never be sure where these links will take you. Often you will click on a link that takes you to a website that looks like one thing but beneath the surface it is running a script and infecting your PC. Be very careful of this and only visit sites that you know and trust. Also never accept a friend invitation from someone unless you know who they are.
5. If a website asks you to install something, get out of there unless you’re sure it’s a genuine plugin like Quicktime, Flash or Silverlight. But even then just go to the official sites and get them from there – you really cannot be too careful. Browsers like FIrefox and Chrome have a good line of defense against this sort of thing, but if you willingly ignore a site’s warning about software installations you let down your
guard. Be vigilant, your browser can only do so much to protect you.
6. Leave Windows update on. Without this option you might as well throw in the towel. A system’s ability to defend itself from internet threats is only as good as the user’s diligence and how up-to-date your machine is. I know it can be annoying when the Windows Update icon appears in the taskbar, especially when you’re in the middle of something. But frankly I’d take that interruption over my credit card info being stolen, or my
computer completely compromised by an internet thief. In the world of internet security, a few comforts need to be sacrificed and Windows Updates is too important to ignore in this day and age. Do so at your
own peril.
Kaspersky Internet Security 2011 offers a number of new and improved
features together with unique protection technologies to address the
latest online threats, keep your PC or Netbook running smoothly and customize protection according to your activities:
-Improved: Risk-based Application Control restricts programs’
rights to access potentially vulnerable system resources or share
sensitive data on the Internet
-New: System Watcher - Heuristics-based analysis monitors, restricts and blocks suspicious program behavior
-Improved: Safe Run mode launches questionable applications and websites without risk
-Improved: Rescue CD disinfects the system after malware attacks
-New: Safe Run for websites mode provides added security for online banking and other similar activities where a high risk of identity theft exists
-Improved: Advanced antimalware technologies even allows installation on infected PCs
-New: New System Watcher technology tracks, records and analyzes suspicious activity and lets you roll back any dangerous actions
-New: Safe Surf technology blocks malware and phishing websites for great online security
 Employers can get into costly trouble over email including private messages sent by employees using company computers and network.
Employers can get into costly trouble over email including private messages sent by employees using company computers and network. This makes it prudent for companies to monitor everything you do on your work computer — and how you communicate in particular. Not only are certain web sites filtered out and your other web activity protocoled minutely; all the emails you send and receive are scanned as well. Routinely, but especially if any legal problems can be foreseen, all mail is archived and catalogued.
Do Not Use Company Computers for Personal Email
When the company watches your every keystroke, you should as well.
- Do not use your company computers, email account and outgoing mail server for private emails.
- If you have your work email account set up at home, use a separate account for private messages. Make sure that private accounts uses a different outgoing (SMTP) server (typically your internet service provider's) to send mail.
- Free email services are reasonably private. Do not use them on company computers or the company network (say, Wi-Fi) for private mail, though.
- You cannot expect any privacy for mail that touches company infrastructure: computers, wired or wireless networks or email (SMTP, IMAP, POP, Exchange, Notes) servers.
a6d0aa94-f8fd-4f0d-9fb1-90deea6de845
1.03.01
ESET NOD32 Antivirus Business Edition v4.2.64.12 (32bit) - Final (Incl. Key Till 2015) | 37 MB
ESET NOD32 Antivirus System - Integrated, Real-Time Protection against viruses, worms, trojans, spyware, adware, phishing, and hackers. Best detection, fastest performance & smallest footprint. NOD32 Antivirus System provides well balanced, state-of-the-art protection against threats endangering your PC and enterprise systems running various platforms from Microsoft Windows, through a number of UNIX/Linux, Novell, MS DOS operating systems to Microsoft Exchange Server, Lotus Domino and other mail servers.
ESET solutions are built on ESET’s one-of-a-kind ThreatSense technology. This advanced heuristics engine enables proactive detection of malware not covered by even the most frequently updated signature-based products by decoding and analyzing executable code in real time, using an emulated environment.
By allowing malware to execute in a secure virtual world, ESET is able to clearly differentiate between benign files and even the most sophisticated and cleverly-disguised malware.
Users of Microsoft® Windows® can experience the power and elegance of NOD32's ThreatSense Technology with ease and comfort. Our single optimized engine offers the best protection from viruses, spyware, adware, phishing attacks, and more. Keep tomorrow's threats at bay with our proactive detection technology.
If you are interested in computer security and would like to get a chance to influence the development of ESET's security systems, we invite you to join our Early Access program. Gain early access to the latest technology in beta and release candidate stages.
Changes in NOD32 Antivirus 4.2.64.12:
* Fix: Computer hangs when going to sleep/hibernate on Windows 7 (usually in combination with Dropbox)
* Fix: Sysrescue Wizard cannot detect the Czech version of Windows Automated Installation Kit
* Fix: Enhanced support of scanning of virtual drives used by Office 2010
* Fix: Opening Office documents from Novell shared folder is not possible
OS: Windows 2K / XP / Vista / XP X64 / Vista64 / 7 / 7 x64
Note: Updated Keys Which expire in The Year 2015-December.
Homepage: http://www.eset.com/
Download from Hotfile:
Association for Computing Home Security
Junaid
On
 There are several things that must be taken to ensure that the use of computers at home (home computing) can be run safely and comfortably.
There are several things that must be taken to ensure that the use of computers at home (home computing) can be run safely and comfortably. 
Three Easy Steps
As a computer user at home, in accessing the Internet through a broadband connection or traditional dial-up use, you should do at least the three following basic security measures to protect the comfort of your home computing process:
1. Antivirus Software installation and maintenance
There are several anti-virus software packages available on the market. This software detects the virus that are recognized by the computer memindal periodically. Most will also check for viruses on incoming email. It is important to update anti-virus software regularly.
2. Update Antivirus
Nearly every day found a new virus. At least once a week you should check the web site vendor that makes anti-virus software to determine whether there is an update available.
3. Do not Open File Unknown or Email
Many viruses and worms are called "social engineering". The point is that these viruses or worms to manipulate you in the process of spreading. Latest virus can appear disguised as an email terkirimdari address, so that it looks like delivered by a person, not by a computer that menginfeksinya. If there was an email from someone you do not know, the easiest way is to immediately delete it without looking. If the email appears to be from someone you know, you should read it carefully before opening any attached files. Viruses and worms often have bad English and grammar. Consider whether the person who you know would write a message or send the attached file. If in doubt, contact the person who you know to confirm they actually sent it before opening the attachment.
Make sure your computer is protected from harmful things. As new viruses are discovered, new vulnerabilities are found. Many of them are in the operating system, like Windows. But viruses are also found in other applications such as web browsers, email software, and various other 3rd party applications. Leaving the computer is open to anyone without a security-protected securities may result in such computers easily disturbed by hackers.
Staying up to date can be difficult. Some software vendors, like Microsoft, have automated utilities that detects whether there is any updates and notify you of other vendors who have a mailing list where you can join and they will notify you of any new updates. If your vendor does not offer one of these solutions, we encourage you to frequently visit the support web site regularly to see if any new patches or updates.
One of the most common questions we get asked by our tech support customers who hire us for virus removal is this: why do people create computer viruses? The answer is a complicated one that involves psychology and the darker side of human nature.
In the interest of simplicity, the word “virus” may sometimes be referring to other types of malware including worms, trojan horses, spyware, adware, and rootkits.
The seven deadly reasons for creating a computer virus:
Boredom: Young people, in this first level of severity, can sometimes simply make poor choices. The ones with inquisitive minds sometimes try their hand at hacking, or “playfully” tinker with joke viruses.
Curiosity: They know it killed the cat, but some people just “need” to find out if their virus will spread. They don’t always realize the damage they do until the virus is “in the wild” and it’s too late.
Revenge: People with very basic coding or hacking skills sometimes join a cause and their motivation is to get back at an individual, corporation, or government.
Greed: Much of the most common malware is designed to get people to pay for bogus software, steal credit card numbers, or even get passwords to take money from bank accounts.
Power: The need for it can be a compelling and destructive force. Hacking and creating viruses to take over computers is never enough; they will always need a bigger thrill.
Aggression: When unchanneled, excessive aggressive traits can be very dangerous to humanity. Think of the videos we have all seen of baseball players with “roid rage.”
Sociopaths: The people likely to create the most destructive types of malware, although they prefer causing physical violence to animals and eventually to people.[1, 2]
Luckily, there are many tech support and antivirus companies trying to put a stop to, or at least slow down the cavalcade of new viruses. There are well over one million viruses now “in the wild.”[3] Computer repair is becoming increasingly more difficult due to rootkit and stealth viruses. To combat these threats, tech support workers must know the inner workings of various versions of Microsoft Windows and have the ability to detect malware without relying on software scanners.
The outsourcing of unqualified support technicians by many of the largest providers is certainly not helping the situation. Unfortunately, virus scanners will never be able to detect all of the current threats, especially since so many people catch them from one wrong click. http://www.youtube.com/watch?v=rnFHMjj5Ly0
Yesterday’s playful teenage hackers are today stealing billions and trying to shut down power grids. [4] [5] That said, there are plenty of “white-hat” hackers who certainly don’t mean any harm. They tend to be bright and not necessarily bad kids who can make some bad decisions, hopefully growing out of it before something bad happens. However, there are no “white-hat” computer virus coders. It is taboo for security firms to write malicious code even to test antivirus software. They are written by those who choose to destroy rather than create.
In the interest of simplicity, the word “virus” may sometimes be referring to other types of malware including worms, trojan horses, spyware, adware, and rootkits.
The seven deadly reasons for creating a computer virus:
Boredom: Young people, in this first level of severity, can sometimes simply make poor choices. The ones with inquisitive minds sometimes try their hand at hacking, or “playfully” tinker with joke viruses.
Curiosity: They know it killed the cat, but some people just “need” to find out if their virus will spread. They don’t always realize the damage they do until the virus is “in the wild” and it’s too late.
Revenge: People with very basic coding or hacking skills sometimes join a cause and their motivation is to get back at an individual, corporation, or government.
Greed: Much of the most common malware is designed to get people to pay for bogus software, steal credit card numbers, or even get passwords to take money from bank accounts.
Power: The need for it can be a compelling and destructive force. Hacking and creating viruses to take over computers is never enough; they will always need a bigger thrill.
Aggression: When unchanneled, excessive aggressive traits can be very dangerous to humanity. Think of the videos we have all seen of baseball players with “roid rage.”
Sociopaths: The people likely to create the most destructive types of malware, although they prefer causing physical violence to animals and eventually to people.[1, 2]
Luckily, there are many tech support and antivirus companies trying to put a stop to, or at least slow down the cavalcade of new viruses. There are well over one million viruses now “in the wild.”[3] Computer repair is becoming increasingly more difficult due to rootkit and stealth viruses. To combat these threats, tech support workers must know the inner workings of various versions of Microsoft Windows and have the ability to detect malware without relying on software scanners.
The outsourcing of unqualified support technicians by many of the largest providers is certainly not helping the situation. Unfortunately, virus scanners will never be able to detect all of the current threats, especially since so many people catch them from one wrong click. http://www.youtube.com/watch?v=rnFHMjj5Ly0
Yesterday’s playful teenage hackers are today stealing billions and trying to shut down power grids. [4] [5] That said, there are plenty of “white-hat” hackers who certainly don’t mean any harm. They tend to be bright and not necessarily bad kids who can make some bad decisions, hopefully growing out of it before something bad happens. However, there are no “white-hat” computer virus coders. It is taboo for security firms to write malicious code even to test antivirus software. They are written by those who choose to destroy rather than create.
Researchers at Internet security service provider CyberDefender looked at some of the most dangerous things you can do online and explained how to protect yourself if you're not quite ready to give up things like Internet porn completely.
Checking the "Keep me signed in" box on public PCs
How to protect yourself:
- NEVER, ever, check the "keep me signed in" box if you're not using your personal laptop or home desktop
- Be careful with work computers. Your office PC might feel "yours" but others can easily snoop when you're away from your desk. They could do something as simple as forward all your messages to their own private email account
- If you just signed IN to Google, eBay, Amazon or other site from a public PC, make sure to sign OFF once you're done
- Delete your browser history from the browser tools when completed to protect your privacy
- Using your browser's privacy mode while browsing prevents information such as the websites you visited from being stored. Internet Explorer 8 calls it "InPrivate Browsing" and Google Chrome calls it a "New incognito window"
- Never save passwords even when prompted to do so by your browser because someone else using your computer later would have access to your accounts
Failing to update Microsoft Windows OS /Java / Adobe Reader / Adobe Flash
How to protect yourself:
- Java / Adobe Reader / Adobe Flash are responsible for an astounding number of PC infections due to security exploits. The best way to avoid becoming a target is to update all three pieces of software as often as you can. Flash will prompt you automatically, but you can tell Java to search for updates daily, instead of bi-monthly. Sign in for automatic updates with Adobe Reader as well
- Make sure to update your windows operating system. One way to do this is to set your windows updates to install automatically. This will reduce your exposure to hackers exploiting vulnerabilities in the windows operating system
Searching for celebrity gossip, incriminating material (i.e. sex tapes)
How to protect yourself:
- This one is a no-brainer. Always be cautious while accessing this material. Malware authors know that people naturally gravitate towards the sex/celebrity combo, so new attacks are targeted specifically towards this crowd
- If you must, search for your news on Google News, Bing News or other aggregator. These services do a basic triage of sites, so chances are you'll be kept from reaching infected blogs/web pages
- When searching on Google use https://www.google.com instead of the common http://www.google.com, which will send your search request through an encrypted SSL connection. CyberDefender has found that doing so reduces the risk of being infected from search results.
Using BitTorrent to download copyrighted software/film/TV shows
How to protect yourself:
- Stick to official downloads/streams such as iTunes, Hulu and legitimate websites. Avoid torrent sites at all costs – even if legit (not malicious), some of the ads found in torrent sites could be compromised. Drive-by downloads are often found in compromised ads and can infect computers without any sort of user input. Visit site -> get infected automatically
- Do not download pirated material
- Do not download pirated material :)
Searching for free porn
How to protect yourself:
- Like everything else "free" on the Internet, free adult content might turn out to be quite expensive. Free porn sites can be downright shady in the way they treat users. That's what makes them ideal targets for bad guys
- Similar to our advice re: torrent sites. The same principle applies here: stick to paid sites. They're interested in keeping users happy, so security will be better. You'll be considerably less exposed to malware this way
Invest in a high-quality security suite such as CyberDefender's Early Detection Center 3.0, which includes - CyberDefender's Link Patrol toolbar. This browser-based utility automatically scans links for malware before users click on them
Online gaming (free to play, social games on Facebook and beyond)
How to protect yourself:
- Be careful when downloading free to play (F2P) clients. If the client software is malicious – or quality assurance happens to be spotty – you could be putting your PC at risk
- Don't give out your login information to strangers. In fact, don't give out ANY kind of information, personal or not, to people you meet gaming. At the very least, you could have your virtual items stolen. At worst, you could lose real money
- Avoid falling for the old "FarmVille Secrets" scam. You will either download a Trojan or expose your Facebook login info to criminals
Leaving Facebook privacy settings wide open, therefore exposing personal info to all
How to protect yourself:
- Carefully review your privacy settings on Facebook. Err on the side of caution – don't let "friends of friends" see your birthday, cell phone number, etc. All of these could be used in an attempt to impersonate you to credit cards, credit unions, etc
- Only friends should have access to the more personal layer of information we all have. So choose your friends wisely – "serial friending" would expose you just as well
Connecting to unknown wireless networks
How to protect yourself:
- In public places, like airports and hotels, be careful about logging into unknown (private) wireless networks. In a hotel for instance, be sure you choose the official one, not another in the neighborhood. Bad guys can eavesdrop as you use your computer, "imitating" a real, safe environment
- Public settings for your laptop are a whole lot more secure – e.g. no file sharing, increased firewall settings, etc
Using the same password for every single online account
How to protect yourself:
- It's hard work to remember several different passwords, so no wonder some use the same password over and over again. But if that one password leaks out to cybercriminals, your entire online life is suddenly open to the world
- Keep different passwords for different purposes. Keep email and social media passwords separate, for example
- Certain browsers can also help with a "master password" that keeps a multitude of passwords in check. So even if you have different passwords for different services, you only have to remember the master password Using a tool (Roboform or Password Vault) for this purpose that encrypts password information and uses best practices to generate passwords is an even better idea
Trying to get a free iPad, PlayStation 3 or similar gadgets (scams/phishing)
How to protect yourself:
- Oldie but goodie: there's no such thing as a free lunch
- If an online offer sounds too good to be true, it usually is
- Avoid any kind of giveaway that's not supported in a big way by a known brand, even if it happens to be an online brand (like Zappos, for example)
- Keep a security suite fully updated, since most of them can catch phishing attempts resulting from this kind of scam
Viruses can be a nuisance, especially if you’ve tried every measure but still find them lurking in some software or hardware piece and significantly affecting your work. And after having tried several antivirus applications, if you still don’t get the desired results, then you’re just left with one final resort–to perform a full PC reinstall. But before you take this drastic measure, there is one more option you should execute. Run a Norton Power Eraser aggressive virus removal scan. However, keep in mind that this program is only to be tried as a last resort, if everything else fails!
On the main interface, you will find two options: Scan for Risks and Undo Past Repair Sessions.
Hit Scan to perform a full system scan.
You can specify location of log file in Settings, which is created to record scan activity. There is also an option to select a detection mode from Normal or Aggressive, by default Normal is selected. According to the product instructions, Aggressive mode is only to be used when all other modes of removing computer threats have exhausted.
A light-weight malware and virus removal application that simplifies the task of destroying viruses; however, the application showed some problem connecting to the Norton server while the scan was being performed. If these bugs are fixed, and if the application manages to quickly install the latest definitions, then this program can certainly prove to be a lot more useful.
It supports Windows 7; testing was carried out on Windows 7 x86 system.
Download Norton Power Eraser
On the main interface, you will find two options: Scan for Risks and Undo Past Repair Sessions.
Hit Scan to perform a full system scan.
You can specify location of log file in Settings, which is created to record scan activity. There is also an option to select a detection mode from Normal or Aggressive, by default Normal is selected. According to the product instructions, Aggressive mode is only to be used when all other modes of removing computer threats have exhausted.
A light-weight malware and virus removal application that simplifies the task of destroying viruses; however, the application showed some problem connecting to the Norton server while the scan was being performed. If these bugs are fixed, and if the application manages to quickly install the latest definitions, then this program can certainly prove to be a lot more useful.
It supports Windows 7; testing was carried out on Windows 7 x86 system.
Download Norton Power Eraser
Great Reasons to Use Anti-Virus Software
Junaid
On
Is your computer secure? Are you really sure of this? The truth of the matter is that it’s very hard to make your computer 100% secure from all the threats that are out there. Yes using a good security suite will help keep your computer secure and safe from 99.9999% of online and offline dangers but no security suite is perfect so you’ll need to use a bit of common sense too when it comes to keeping your computer and its data safe.
There’s a lot of stuff you need to protect your computer from – spam, viruses, worms, spyware, phishing and other similar hacking attempts. If you leave your computer unsecured online it’s only a matter of time before you get attacked or infected. Actually guess how long it takes a new computer to get infected from an online source? No more than 2 hours…120 minutes. That’s all the time it takes for your shiny new computer to be riddled with viruses and spyware.
Anytime I see people using a computer with no virus or firewall protection I actually feel like crying because I know what’s going to happen. Then I get the phone call asking for help in fixing the problem.
You have a choice of either buying several separate security products and installing them one at a time or you can install a single suite that does it all for you. For most new users a suite is ideal because it’s less to worry about.
So how do you go about choosing your perfect computer security suite?
Total Protection
Whatever product you choose make sure it gives you the most bang for your buck – you want total protection for your computer for one single price. Ideally the software should include antivirus protection, a firewall and spyware protection at the minimum. Any other bells and whistles that are included are all well and good but make sure that your basic security needs are covered here.
Read Reviews
Never buy any product without reading a few user reviews first. Magazine reviews are fine but can be a bit biased so try to find real user comments on how well the software suite works. You can try Zdnet.com and PCMag.com for reviews of all the latest and great security suites – plus you’ll get to see user feedback at the end of the reviews.
Brand Names
If you’re stuck for making a choice then try to stick to a brand name that you recognize. Good example are Norton, Kaspersky and Zonelabs(the Zonealarm people). Combined with reading a handful of user reviews you’ll be able to make your mind up pretty quickly.
System Requirements
Always check the minimum requirements for any piece of software you buy. Remember that minimum means just that – those requirements listed are what the software needs to run. If you’re just meeting the minimum requirements then everything should work but will just do it really slowly.
Do you know how many risks exist online? Without proper computer security software your computer will be attacked or infested within 2 hours of being online! Get more internet and computer security tips here -> http://www.cpusecurity.com
There’s a lot of stuff you need to protect your computer from – spam, viruses, worms, spyware, phishing and other similar hacking attempts. If you leave your computer unsecured online it’s only a matter of time before you get attacked or infected. Actually guess how long it takes a new computer to get infected from an online source? No more than 2 hours…120 minutes. That’s all the time it takes for your shiny new computer to be riddled with viruses and spyware.
Anytime I see people using a computer with no virus or firewall protection I actually feel like crying because I know what’s going to happen. Then I get the phone call asking for help in fixing the problem.
You have a choice of either buying several separate security products and installing them one at a time or you can install a single suite that does it all for you. For most new users a suite is ideal because it’s less to worry about.
So how do you go about choosing your perfect computer security suite?
Total Protection
Whatever product you choose make sure it gives you the most bang for your buck – you want total protection for your computer for one single price. Ideally the software should include antivirus protection, a firewall and spyware protection at the minimum. Any other bells and whistles that are included are all well and good but make sure that your basic security needs are covered here.
Read Reviews
Never buy any product without reading a few user reviews first. Magazine reviews are fine but can be a bit biased so try to find real user comments on how well the software suite works. You can try Zdnet.com and PCMag.com for reviews of all the latest and great security suites – plus you’ll get to see user feedback at the end of the reviews.
Brand Names
If you’re stuck for making a choice then try to stick to a brand name that you recognize. Good example are Norton, Kaspersky and Zonelabs(the Zonealarm people). Combined with reading a handful of user reviews you’ll be able to make your mind up pretty quickly.
System Requirements
Always check the minimum requirements for any piece of software you buy. Remember that minimum means just that – those requirements listed are what the software needs to run. If you’re just meeting the minimum requirements then everything should work but will just do it really slowly.
Do you know how many risks exist online? Without proper computer security software your computer will be attacked or infested within 2 hours of being online! Get more internet and computer security tips here -> http://www.cpusecurity.com
USB Security Utilities 1.0 is a utility which controls and protects USB drives such as pendrive, removable hard disk etc. It has a strong scanning engine which helps to analyze the memory or a folder. It is small in size and portable and can be installed in any portable device. It will also detects dangerous files and draw backs as well as handling various functions in one single window.
USB Security Utilities 1.0 Features
- Small in size and portable
- Can be installed in various portable device
- Supports Strong Scanning Engine
- Detects dangerous files
- Can view device information
- Multilanguage interface
- Simple to use
- Strong detection ability
- Prevents infection of device
Private browsing: it's not so private
Junaid
On

Research by Stanford University to investigate the privacy of the "private browsing" feature of many Web browsers suggests that the tools aren't all that private after all, and that many kinds of information can be leaked by browsers when using the mode. The paper is due to be presented next week at the USENIX security conference.
"InPrivate Browsing" in Internet Explorer, "Incognito mode" in Chrome, and "Private Browsing" in Firefox and Safari all strive to do the same two things: make it impossible for users of the same computer to figure out which sites the browser has been used to visit, and make it impossible for sites to know whether or not a particular user has previously visited them.
To keep browsing private from other users of the same machine, browsers must discard (or avoid creating) any history entries, cached items, cookies, and so on. To prevent sites from being able to track visitors, the browsers must ensure that they don't send any cookies or other identifiable information from non-private sessions when in private mode.
The researchers found that the browsers' protections were imperfect. Browsers did not properly isolate their private sessions from non-private ones, with the result that suitably crafted sites could trace visitors between private and non-private sessions. Sites could also leave persistent indications that they had been visited, allowing visits to be detected by local users.
One example of such a plugin used to be Adobe Flash; Flash has its own cookie system, and it used to be the case that Flash's cookies did not respect the privacy mode of the browser. Cookies set in private mode persisted, and cookies set in public mode were readable from private mode. Fortunately, Flash has since been fixed, but any plugin could contain similar errors.
Internet Explorer and Chrome both disable browser extensions by default in their private mode; Firefox, however, does not, and this provides yet another avenue by which private information can be leaked.
As part of their research, the team also collected information on how often people use private modes. Though Microsoft advertises InPrivate Browsing as a way for people to buy gifts online without any risk that the recipient will find out, the most common use of private browsing was (shockingly) to explore the Internet's seedy underbelly, keeping prurient interests, rather than birthday presents, private. Even this use was relatively rare; only 8 percent of people used private browsing for their online sexual entertainment, with 6 percent using it for gift shopping and general Web browsing.
The use of private browsing also varied wildly between browsers. Internet Explorer users barely bothered—just 2 percent of them use it, even for X-rated sites—whereas some 14 percent of Safari users prefer to keep their dirty/gift-buying habits to themselves.
"InPrivate Browsing" in Internet Explorer, "Incognito mode" in Chrome, and "Private Browsing" in Firefox and Safari all strive to do the same two things: make it impossible for users of the same computer to figure out which sites the browser has been used to visit, and make it impossible for sites to know whether or not a particular user has previously visited them.
To keep browsing private from other users of the same machine, browsers must discard (or avoid creating) any history entries, cached items, cookies, and so on. To prevent sites from being able to track visitors, the browsers must ensure that they don't send any cookies or other identifiable information from non-private sessions when in private mode.
The researchers found that the browsers' protections were imperfect. Browsers did not properly isolate their private sessions from non-private ones, with the result that suitably crafted sites could trace visitors between private and non-private sessions. Sites could also leave persistent indications that they had been visited, allowing visits to be detected by local users.
The big problem: add-ons
The problem got worse when extensions and plugins were considered. All four browsers tested enabled plugins in private mode, and these plugins can themselves store data that allows both kinds of privacy to be defeated.One example of such a plugin used to be Adobe Flash; Flash has its own cookie system, and it used to be the case that Flash's cookies did not respect the privacy mode of the browser. Cookies set in private mode persisted, and cookies set in public mode were readable from private mode. Fortunately, Flash has since been fixed, but any plugin could contain similar errors.
Internet Explorer and Chrome both disable browser extensions by default in their private mode; Firefox, however, does not, and this provides yet another avenue by which private information can be leaked.
As part of their research, the team also collected information on how often people use private modes. Though Microsoft advertises InPrivate Browsing as a way for people to buy gifts online without any risk that the recipient will find out, the most common use of private browsing was (shockingly) to explore the Internet's seedy underbelly, keeping prurient interests, rather than birthday presents, private. Even this use was relatively rare; only 8 percent of people used private browsing for their online sexual entertainment, with 6 percent using it for gift shopping and general Web browsing.
The use of private browsing also varied wildly between browsers. Internet Explorer users barely bothered—just 2 percent of them use it, even for X-rated sites—whereas some 14 percent of Safari users prefer to keep their dirty/gift-buying habits to themselves.
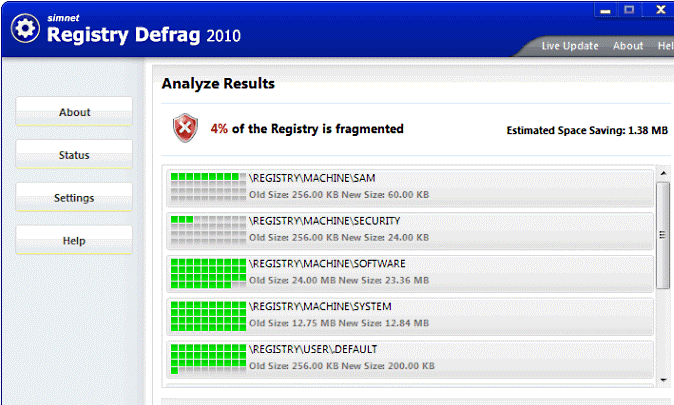
Simnet RegDefrag is yet another tool to defragment your registry. It quickly scans your registry and provides you with an overview that shows which parts of the registry are defragmented and to what extend. The program will create a System Restore point before it starts the defrag process, so you can undo the changes if you run into problems. By using Simnet Registry Defrag periodically, you improve your system’s performance, prevent registry corruption, compact and optimize windows registry.
Features:
* Automatic system restore points for safety.
* Automatically product update.
* Smart and easy-to-use interface.
* Minimal installation, low memory and cpu usage.
Download Simnet Registry Defrag
Features:
* Automatic system restore points for safety.
* Automatically product update.
* Smart and easy-to-use interface.
* Minimal installation, low memory and cpu usage.
Download Simnet Registry Defrag
 Windows only: CCleaner Enhancer updates the popular system cleaning utility with support for cleaning up after 270 more applications, so you can keep your system even more crap free.
Windows only: CCleaner Enhancer updates the popular system cleaning utility with support for cleaning up after 270 more applications, so you can keep your system even more crap free.Once you've downloaded and started the utility, your CCleaner installation will be updated with support for the extra applications—you'll be prompted to select the folder to install the rules in if you're using a portable version. You'll find the new rules on the Applications tab in CCleaner—readers should note that you won't actually see 270 new rules in the list, since you'll only see rules that actually apply to your system and installed applications.
CCleaner Enhancer is a free download for Windows only. If you're new to CCleaner, make sure to check out how to run CCleaner on a schedule to keep your PC crap-free automatically, or create a shortcut to run CCleaner silently.
Update: Looks like the web site died under the weight of Lifehacker's readers. Here's a mirror copy of the zipped download file.
 Passwords are your first and last line of defense. Most people do not seem to understand the importance of this tool. It’s only when their account is hacked, password is stolen or some security is compromised with, that they bother to exercise due care in dealing with passwords. Creating an ultra-strong password and not sharing it with world is all it takes to be safe on the web.
Passwords are your first and last line of defense. Most people do not seem to understand the importance of this tool. It’s only when their account is hacked, password is stolen or some security is compromised with, that they bother to exercise due care in dealing with passwords. Creating an ultra-strong password and not sharing it with world is all it takes to be safe on the web.Here’s a guide that will help you create an easy-to-remember but strong password.
Essentials of a good password
- Password should at least be 8-10 characters long.
- Passwords should be a combination of numbers and letters.
- Letters should be both capital and small.
- At least one symbol or special character should be present.
Steps to create a strong password
- Step 1. Select A Sentence: First step is to select an 8-10 words sentence. The important thing to keep in mind here is that the sentence should not be obvious or guessable. Any random sentence is good enough. Do not take guessable and/or short sentences like “I first name is XYZ“, etc. For the purpose of explaining, we will take the first line of this post as the sentence.“Passwords are your first and last line of defence”.
- Step 2. Trimming the words into characters: Reduce the words to their first letters. For example, “Passwords” can be reduced to “p“. Also, words like “are” can be changed to “r“, So our sentence gets reduced in the following manner:Passwords [p] are [r] your [y] first [f] and[a] last[l] line[l] of[o] defence[d]
Now, the password looks like this: pryfallod
- Step 3. Insert Numbers: As said before, a good password has both, numbers & alphabets. So to get numbers, we can do two things. Firstly, the word in Step 1 can be represented by numbers. In our example, “first” in the sentence can be represented by “1” instead of “f“. Secondly, letters in Step 2 can be converted into numbers which look similar. In the present case, the second last letter “o” can be changed to “0[zero]. Similarly you can substitute ” l” for “1“.After this step, our password turns into: pry1all0d
- Step 4. Capital & Small Cap Letters: Some of the letters in the password have to be capitalized. Now we arrive at the question, which ones? The first and last letter can be selected. Or, perhaps, those letters can be selected which are more prominent or more important. In our case, “passwords” and “defence” happen to be the most prominent words in the sentence. These words need not be at the end or start of the sentence.Now our password looks like: Pry1all0D
- Step 5. Special Characters or Symbols. Symbols lend and extra level of security to the password and make it nearly impossible to crack. One can randomly add a special character to the password or follow the same method that one did in Step 3 with numbers.For instance, “l” can be replaced with “!” or “a” can be replaced with “@“. Or randomly substitute letters with symbols like changing “y” with “$“.
Final password: Pry1al!!d
 Now, this password is really difficult to crack. Looking at it, one may think that it would be really hard to memorize such a password. However, it isn’t that hard to remember it. In fact, by the time I complete writing the article, I myself have memorized the password. Moreover, even if you forget the password, you’ll always have the original sentence to help you recall the password.
Now, this password is really difficult to crack. Looking at it, one may think that it would be really hard to memorize such a password. However, it isn’t that hard to remember it. In fact, by the time I complete writing the article, I myself have memorized the password. Moreover, even if you forget the password, you’ll always have the original sentence to help you recall the password.
Now that you have a good password, here are a couple of things you should take care of;- You should never share password with somebody else, not even your best buddy or spouse.
- You should never write down your password anywhere, neither on a paper nor in notepad or document file.
Take care and secure yourself.
Change WordPress login page URL
Junaid
On
As you might know, the default login page in WordPress is domain/wp-login.php. Almost every other person in the world knows that it is the login page of a WordPress blog. So if someone gets yourpassword, it is easy for them to login to your WordPress dashboard and change the default password. Trial & error and brute force attacks by bots on a particular page would also lead to password theft. Stealth Login is a WordPress plugin that can be used to change WordPress login URL to custom URL and prevent such incidents.
Stealth Login is a WordPress plugin :
Stealth Login WordPress plugin options:
Download the plugin here, upload to the WordPress plugin directory and activate. As you can see from the screenshot, there is a simple option to customize WordPress login slug. First, turn the plugin ON and enter the required login URL slug in the login slug box. Now enable stealth mode and save changes. Plugin will start working from the next login.
Stealth Login is a WordPress plugin :
Stealth Login WordPress plugin options:
Download the plugin here, upload to the WordPress plugin directory and activate. As you can see from the screenshot, there is a simple option to customize WordPress login slug. First, turn the plugin ON and enter the required login URL slug in the login slug box. Now enable stealth mode and save changes. Plugin will start working from the next login.
Here is how a keylogger
works
- By recording each keystroke and immediately dispatching it to remote listener over internet
- By collecting keystrokes data in a temporary file and then uploading it via internet
- The collected keystrokes are never sent via internet instead they are collected in a temporary file and then if someone has access to your system either physical or remote they collect this data manually.
- Finally the hardware keyloggers: these are actually hardware devices that include a little flash memory to record all your keystrokes,and then the person collects this data manually
So why do I need a Anti Keylogger when I have an
Antivirus?
Well I agree that most anti viruses offer or at least claim to offer security against keyloggers,but here comes the interesting part why not test your anti-virus below is a link to a small software that will check whether you are secure or not. Run various tests in it and then you will see how easily it records your keystrokes and desktop screen-shots.
bit.ly/94QGxB
So i hope now you know why you need a anti keylogger.
bit.ly/94QGxB
So i hope now you know why you need a anti keylogger.
It’ also available as a firefox addon. https://addons.mozilla.org/en-US/firefox/addon/3383/
For more info visit their website : http://www.qfxsoftware.com
The word Proxy is derived from a Latin word proximus which means “close”.A proxy is actually a server which helps us maintaining our privacy on the Internet. It is just like a wall between you and the Internet. When you use a proxy, the webpage on the other side won’t be able to see you, webpage interacts with the proxy and proxy in return shows us the webpage. In this way a proxy server works. A client connects to the proxy server, requesting some service, such as a file, connection, web page, or other resource, available from a different server. The proxy server evaluates the request according to its filtering rules.
For example, it may filter traffic by IP address or protocol. If the request is validated by the filter, the proxy provides the resource by connecting to the relevant server and requesting the service on behalf of the client. A proxy server may optionally alter the client’s request or the server’s response, and sometimes it may serve the request without contacting the specified server.
A proxy server that passes requests and replies unmodified is usually called a gateway or sometimes tunneling proxy.A proxy server can be placed in the user’s local computer or at various points between the user and the destination servers on the Internet.
A reverse proxy is (usually) an Internet-facing proxy used as a front-end to control and protect access to a server on a private network, commonly also performing tasks such as load-balancing, authentication, decryption or caching.
Human is the most weakest part of the Information Security chain. Psychologists have identified many benefits people receive when they help others. Helping can make us feel empowered. It can get us out of a bad mood. It can make us feel good about ourselves. Hackers find many ways of taking advantage of our inclination to be helpful.
 | |
| Click Image To Enlarge |
Because Hackers often target people who don’t know the value of the information they are giving away, the help may be seen as carrying little cost to the helper. Most of Humans tend to explain thier behaviour and of others, while doing this we give away alot of information about us.
Security is too often merely an illusion, an illusion sometimes made even worse when gullibility, naivete, or ignorance come into play. The world’s most respected scientist of the twentieth century, Albert Einstein, is quoted as saying, “Only two things are infinite, the universe and human stupidity, and I’m not sure about the former.” In the end, social engineering attacks can succeed when people are stupid or, more commonly, simply ignorant about good security practices.
With the same attitude as our security-conscious homeowner, many information technology (IT) professionals hold to the misconception that they’ve made their companies largely immune to attack because they’ve deployed standard security products – firewalls, intrusion detection systems, or stronger authentication devices such as time-based tokens or biometric smart cards.
Anyone who thinks that security products alone offer true security is settling for. the illusion of security. It’s a case of living in a world of fantasy: They will inevitaby, later if not sooner, suffer a security incident
Download UltraSurf 9.97 Free
Junaid
On
UltraSurf is a small application which protects your Internet privacy withanonymous surfing and browsing -- hide IP addresses and locations, clean browsing history, cookies & more.UltraSurf is a free software which enables users inside countries with heavy Internet censorship to visit any public web sites in the world safely and freely. Users in countries without internet censorship also use it to protect their internet privacy and security.
With UltraSurf started, you can use web browsers (like IE, Firefox) the same as before, but all are under UltraSurf's protection now.UltraSurf 9.97 is one of the best software to surf internet.
Facts of UltraSurf:
* Service provided for 6 years
* Millions of users
* Users from over 150 countries
* Daily hits over 300 million
* Daily traffic over 5,000 GB
Features:
* No installation required
* Easy to use
* Deletes all browsing traces automatically

With UltraSurf started, you can use web browsers (like IE, Firefox) the same as before, but all are under UltraSurf's protection now.UltraSurf 9.97 is one of the best software to surf internet.
Facts of UltraSurf:
* Service provided for 6 years
* Millions of users
* Users from over 150 countries
* Daily hits over 300 million
* Daily traffic over 5,000 GB
Features:
* No installation required
* Easy to use
* Deletes all browsing traces automatically